We are dedicated to safeguarding your digital property through cutting-edge network and cybersecurity solutions. With a team of seasoned experts and a commitment to excellence, we offer
comprehensive services tailored to meet the evolving challenges of today’s cyber landscape.
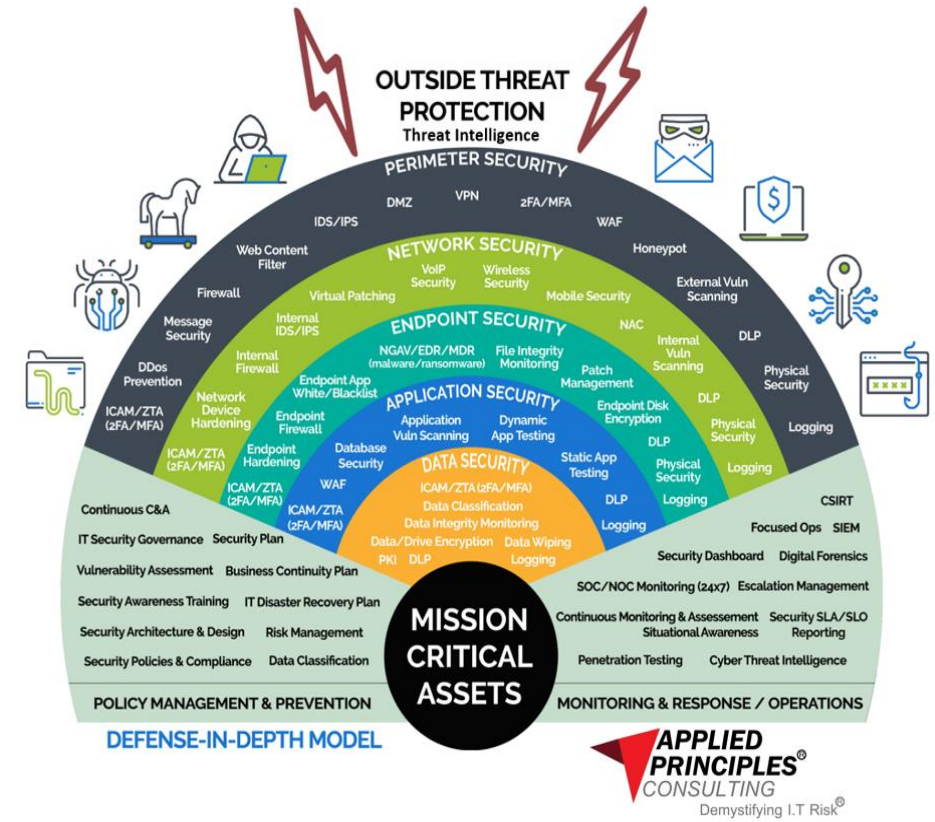
Our wide range of security product solutions are selected to provide comprehensive network and ICT infrastructure security to businesses of all sizes. Our team of experts will assist you in conducting thorough security reviews, and deploying robust cybersecurity solutions tailored to your specific needs. Our response takes a multi-tiered approach based on the circle-of-trust / line-of-defense methodology.
Perimeter Security
We refer to as perimeter security the control and secure access to and from your organizations’ network and all its assets therein. This is the first line of defense against unauthorized access and potential threats from external sources and as well as control of internet resources accessed by your network. Some of the solutions focused at this layer include; Perimeter Firewalls, Anti DDOS solution, Email Security, VPN & VPN security, Web Application Firewall (WAF)
Network Security
In this digitized era – interconnected world, network security forms the foundation of a robust cybersecurity strategy. At Applied Principles, we understand the critical importance of securing your network infrastructure against potential threats. The “Network” is the backbone of your business. We, therefore, take an extended approach. First, our team will work with you to establish the maturity of your network and then design a strategy to ensure that a clear network security growth plan is established.
Endpoint Security
Endpoints and Servers are in every organization running multiple flavors of operating software. If a cyber-attack is to get into the company, either an endpoint or server will be a target. It is therefore mission-critical to ensure that these assets are protected. Telemetry from these assets also ensures that security teams have visibility of attack attempts, impending attacks, vulnerable endpoints and servers, and more.
Application Security
Most organizations utilize applications to interact with digitized data. These applications are selfhosted on-premise, in the cloud – sometimes multi-cloud, and in some instances a hybrid approach. These architectures are chosen to ensure seamless digital transformation. It is paramount that such digital companies deploy automated protection to these assets.
Applied Principles’ team of experts will work with you to ensure that security solutions designed and deployed at the application line of defense make such attacks as Website hacking, Illegal content injection to your website, Account takeovers, unknown zero-day threats, and more a thing of the past!
Data Security
For all organizations, Data in all aspects is the holy grail – Gold if you may. Most cyber-attacks target that data and then monetize it by ransom demands, and reputational blackmail. Some instances involve the theft of intellectual data that hold the company’s market edge and more. Our team will work with you to expose the gaps, and design and implement data security solutions to ensure that one, there is visibility where all data resides, and two secure it.